What's in a scam? Part 1 of 3

Here is a talk I am giving about protecting yourself from scams, I wanted to share it with the world:

The purpose of this presentation is to provide a high-level overview of common scams and how to protect yourself.

The mantra for this talk is "it is not about age, we do not victim blame, scammers are from all over the world." The point of this is to:
- Shift the focus away from "older" people as the primary victims of scams. This is simply not true, it is ageist, and most of all it gives "younger" people a false sense of security.
- Victim blaming is rampant in cybersecurity and in the zeitgeist around scams. Stop it. The blame rests solely on the criminals perpetrating these scams, NOT the victims.
- Let's stop being xenophobic about scammers. Yes, there are a lot of Nigerian Princes out there people, but let's not conflate the ENTIRE nation of Nigeria with scams. There are a lot of scam call centers in India, but there are also a lot of call centers in India - it is a crime of opportunity built on the backs of cheap labor.

Here, I talk about a few broad categories of fraud that encapsulate a lot of the scams out there, but certainly not all of it. Here, the goal is to focus on fraud targeting individuals, not organizations, but it is important to note that as an individual who is a part of an organization - you may also be targeted in that capacity.
Consumer investor fraud - examples include Bitcoin, NFT's, or other Ponzi schemes based upon securities or other speculative "investments". Anything with "the blockchain" in it should immediately stink of scam.
Consumer products and services fraud - credit repair scams ("We'll fix your credit for $1000 in 30 days or less), vacation/rental housing scams, Facebook marketplace / eBay scams.
Employment fraud - nanny scams, money-muling, basically any scam involving employment as a pre-text to the fraud.
Prize or “grant” fraud - Sweepstakes, lottery fraud, government grant offers, Nigerian letter scams, advance fee scams.
Phantom debt collection fraud - IRS back taxes, obituary scams, fake medical debt, fake loan debt.
Charity fraud - Current events, natural disasters, crowdfunding sites, law enforcement charities.
Relationship fraud - Romance scams, friend/relative imposter scams, “grandparent scam”.
I did not make up this taxonomy of fraud, you can read more about one version of this here: https://www.finrafoundation.org/sites/finrafoundation/files/framework-taxonomy-fraud.pdf
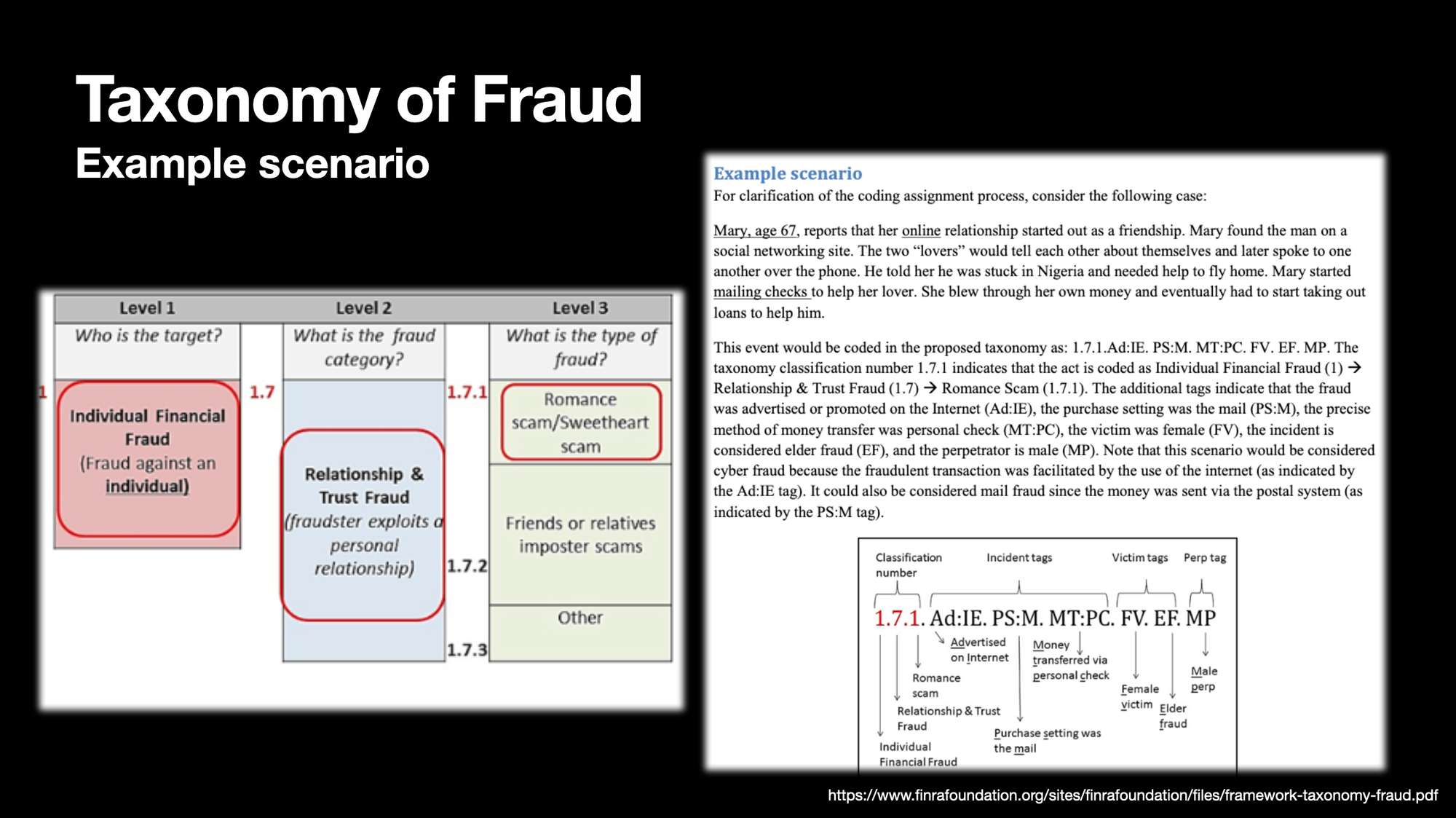
Example scenario: ...Mary, age 67, reports that her online relationship started out as a friendship. Mary found the man on a social networking site. The two "lovers" would tell each other about themselves and later spoke to one another over the phone. He told her he was stuck in Nigeria and needed help to fly home. Mary started mailing checks to help her lover. She blew through her own money and eventually had to start taking out loans to help him.
This event would be coded in the proposed taxonomy as: 1.7.1.Ad:IE. PS:M. MT:PC. FV. EF. MP. The taxonomy classification number 1.7.1 indicates that the act is coded as Individual Financial Fraud (1) → Relationship & Trust Fraud (1.7) → Romance Scam (1.7.1). The additional tags indicate that the fraud was advertised or promoted on the Internet (Ad:IE), the purchase setting was the mail (PS:M), the precise method of money transfer was personal check (MT:PC), the victim was female (FV), the incident is considered elder fraud (EF), and the perpetrator is male (MP). Note that this scenario would be considered cyber fraud because the fraudulent transaction was facilitated by the use of the internet (as indicated by the Ad:IE tag). It could also be considered mail fraud since the money was sent via the postal system (as indicated by the PS:M tag).
I highlight this bit from FINRA merely to give an example of how this taxonomy comes into play. While I don't think this taxonomy is particularly useful outside of law enforcement, I think it is important to understand there is nuance and depth here, and accepted terminology exists.
To be continued...
Part 2 link here
This blog © 2024, by Sean Halloran is licensed under CC BY-NC 4.0

